In the digital age, where security and technology intertwine seamlessly, understanding precise terminology is more critical than ever.
Two terms often confused or misused in the tech world are “Authentication” and “Authentification.”
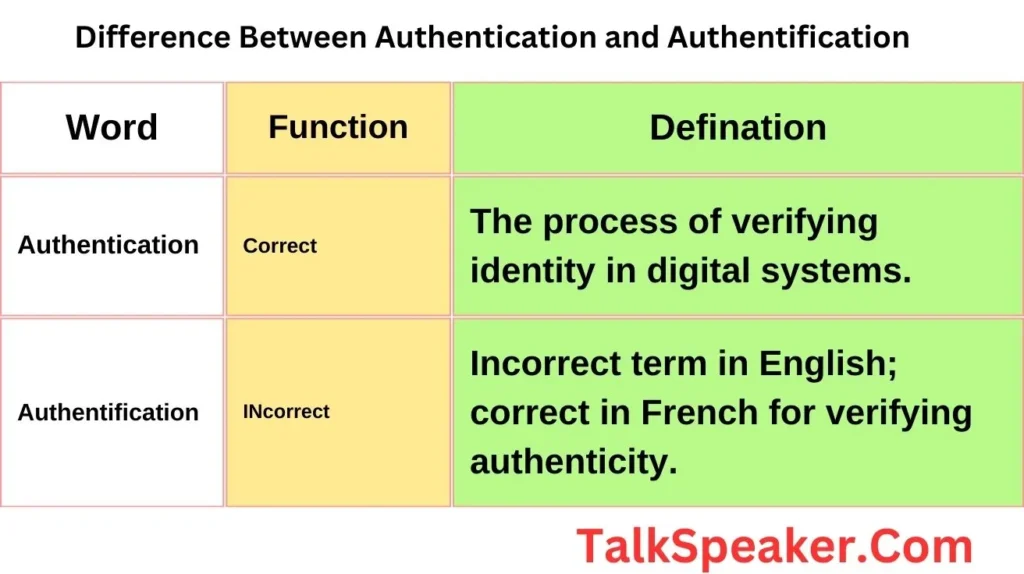
“Authentication” is the right term in English; “Authentification” is a common error influenced by French.
While they may seem similar, they carry distinct meanings and implications. This comprehensive guide delves into these terms, exploring their origins, proper usage, and their significance in the realm of cybersecurity.
Difference Between Authentication and Authentification
| Term | Definition | Example |
|---|---|---|
| Authentication | The process of verifying identity in digital systems. | Logging into an email account with a password. |
| Authentification | Incorrect term in English; correct in French for verifying authenticity. | Used in French legal documents for identity checks. |
Why Words Matter in Technology
Importance of Precise Terminology in Tech
In the rapidly evolving world of technology, the precise use of terminology is not just a matter of semantics; it’s a necessity.
Misunderstanding or misusing terms can lead to confusion, miscommunication, and even security vulnerabilities.
When it comes to cybersecurity, using the correct terms ensures that everyone, from developers to end-users, is on the same page.
Overview of Common Confusions
The terms “Authentication” and “Authentification” are often used interchangeably, but this is a mistake. The confusion stems from their similar appearance and the technical context in which they are often discussed.
However, understanding the difference between these two terms is crucial for anyone involved in digital security.
What is Authentication? A Key Security Concept
Definition and Significance
Authentication is the process of verifying the identity of a user, device, or entity in a digital system. This verification ensures that the person or system accessing the information is who they claim to be.
Authentication is a fundamental concept in cybersecurity, forming the first line of defense against unauthorized access.
“Authentication is the process of confirming that something (or someone) is, in fact, who or what it is claimed to be.”
Real-World Applications
Authentication is everywhere in our digital lives. From logging into your email account to accessing a bank’s online services, authentication plays a critical role in protecting sensitive information.
Here are some common real-world applications:
- Email Accounts: Verifying a user’s identity before granting access to personal or work-related emails.
- Online Banking: Ensuring that only authorized users can perform transactions.
- Secure Websites: Protecting data exchanges between a user and a website using SSL/TLS certificates.
Authentication Types and Methods
Authentication methods have evolved significantly, especially with the rise of digital threats. Below are some of the most common types:
| Type | Description | Examples |
| Password-Based | Requires a username and password combination. | Login credentials for email accounts. |
| Two-Factor Authentication | Combines two different authentication methods, such as something you know (password) and something you have (phone). | Bank OTPs sent to a mobile phone. |
| Biometric | Uses unique biological traits to verify identity. | Fingerprint scanners, facial recognition. |
| Token-Based | Uses a physical device or token that generates a one-time code. | RSA SecurID tokens, Google Authenticator app. |
The Myth of ‘Authentification’: Where It Went Wrong
Origins of the Misunderstanding
The term “Authentification” often appears in discussions about security, but it is a misnomer in English. The confusion likely arises from the influence of other languages, where similar terms are used correctly.
However, in English, “Authentification” is incorrect and should be avoided in professional and technical contexts.
Linguistic Perspective
From a linguistic standpoint, “Authentification” is a malformed word in English.
It seems to combine the idea of “authentication” with unnecessary suffixation, leading to a term that does not align with English word formation rules.
Impact of Misuse
Using “Authentification” instead of “Authentication” can lead to several issues:
- Miscommunication: Professionals might misunderstand instructions or documentation, leading to errors in implementation.
- Perception of Expertise: Using incorrect terminology may cause others to question the speaker’s or writer’s expertise.
- Documentation Errors: Inconsistent terminology in official documents can lead to legal and operational risks.
‘Authentification’ in Other Languages: The French Connection
Authentification in French
In the French language, “Authentification” is a legitimate word used to describe the process of verifying the authenticity of something.
It aligns with the French word-formation rules and is commonly used in contexts such as legal documents, identity verification, and more.
Cross-Linguistic Confusion
The term “Authentification” has crept into English due to cross-linguistic influences, especially in regions where both French and English are spoken. This blending often leads to the incorrect adoption of the term in English, where “Authentication” should be used instead.
Comparing French and English Usage
In French:
- “Authentification” refers to the verification process, similar to “Authentication” in English.
In English:
- “Authentication” is the correct term for the process of verifying identity or authenticity.
| Language | Correct Term | Context |
| English | Authentication | Verifying identity in security. |
| French | Authentification | Verifying authenticity. |
How to Remember the Correct Term: Spelling Tips and Tricks
Mnemonic Devices
To avoid confusion, you can use simple mnemonic devices. For example:
- “Authentication is Authentic.” Remembering that the root of the word is “authentic” can help recall that “Authentication” is the correct term.
Contextual Clues
Consider the context in which you are using the term:
- If you are discussing identity verification in cybersecurity, “Authentication” is the word you need.
- In non-English languages, especially French, “Authentification” may be correct.
These simple clues can help you choose the right term based on the situation.
Authentication in the Digital Age: Importance and Methods
Role in Cybersecurity
Authentication is not just a security measure; it is a critical component of maintaining the integrity and confidentiality of digital systems. It prevents unauthorized access, ensuring that sensitive information remains secure.
Modern Techniques
As digital threats evolve, so too do authentication methods. Here are some of the most current techniques:
- Multi-Factor Authentication (MFA): Requires two or more verification methods, such as a password and a fingerprint, making unauthorized access significantly harder.
- Biometric Authentication: Uses unique biological characteristics like fingerprints or retinal scans to verify identity, making it difficult for unauthorized users to gain access.
- Behavioral Authentication: Analyzes user behavior patterns, such as typing speed or mouse movement, to verify identity.
Challenges and Future Trends
While authentication is vital, it also faces challenges:
- Phishing Attacks: Even with robust authentication methods, phishing remains a significant threat, tricking users into revealing their credentials.
- Social Engineering: Attackers manipulate individuals into breaking standard security practices, often bypassing authentication measures.
Looking forward, the future of authentication may include:
- Zero-Trust Security Models: A security framework that assumes any user could be compromised and continually validates authentication throughout a session.
- Decentralized Authentication: Using blockchain technology to create a secure, tamper-proof authentication process.
User Experience vs. Security: Balancing Authentication
The UX-Security Trade-Off
Balancing user experience (UX) with security is a persistent challenge in cybersecurity. While strong authentication methods enhance security, they can sometimes hinder user experience by adding complexity to login processes.
Case Studies
Here are a few examples where companies have successfully balanced UX with security:
- Apple’s Face ID: This facial recognition technology provides strong security while offering a seamless user experience.
- Google’s 2-Step Verification: This method increases security without overly complicating the user experience by using push notifications instead of codes.
Future of Authentication in UX Design
As technology advances, we can expect to see authentication processes that are both secure and user-friendly. Innovations may include:
- Context-Aware Authentication: Systems that adapt the level of authentication required based on the user’s behavior and context, such as location or time of day.
- Invisible Authentication: Seamless authentication processes that operate in the background, reducing friction for the user.
People Questions
1. What is the difference between Authentication and Authentification?
Authentication is correct in English; Authentification is a French term.
2. Why is Authentication important?
It secures systems by verifying user identity.
3. Is Authentification a valid word?
No, it’s not correct in English.
4. What are common Authentication methods?
Passwords, biometrics, tokens, and two-factor authentication.
5. How can I remember the right term?
Think: “Authentication is authentic.”
Conclusion
Summary of Key Points
In summary, Authentication is a crucial concept in cybersecurity, while “Authentification” is a term that has caused confusion due to its misuse in English.
Understanding the difference between these terms ensures clear communication and robust security practices.
The Role of Education in Terminology
Educating yourself and others about the correct use of terms like “Authentication” is vital in the tech industry.
Proper terminology enhances understanding and prevents potential security risks.
Final Thoughts on Language and Technology
Language plays a significant role in how we understand and implement technology.
By using precise terms and continually educating ourselves, we contribute to a more secure and efficient digital world.

Sophie Mitchell, a seasoned English educator, brings her passion for language and years of teaching expertise to TalkSpeaker. With a knack for simplifying grammar and expanding vocabulary, she empowers learners to master English with confidence.